
Information Security, Cybersecurity and System Availability
Challenges and Commitments
Information technology has developed rapidly in the past years and plays a significant role in the business operations of organizations worldwide. This has resulted in cybersecurity threats being considered as a critical risk and challenge for global organizations. Therefore, GGC is well aware of the risks relating to information technology and cyber security which present themselves in the forms of obstacles from external attacks on the IT system or internal leakage of personal and corporate data. Such risks can affect GGC’s operations and the safety of the personal data of employees, customers and suppliers. Therefore, GGC strives to develop a system that creates an IT shield through a secure governance structure and compliance with the Personal Data Protection Act as well as trainings to create confidence, knowledge and understanding for employees.
Key Stakeholders
Employee
Customer
Government
Supplier and Business Partner
Goals
of personal data, no complaints relating to cyber security incidents, and no employees or stakeholders fall victim to IT and cyber-attacks.
Management Approach
Cybersecurity Governance
GGC has established a policy for information technology security to be used as a guideline for the development of information security management systems and have a process of controlling the security of information technology systems according to standard ISO 27001: Information Security Management and Control Objectives for Information and Related Technologies (COBIT). This covers the procedures regarding the use of information (Procedure) in order to manage operations for information and cyber securities, as well as to prevent and reduce risks and potential impacts.
In addition, GGC has established an information security and cyber security governance structure, which is regarded as the main process in building information security and protection against cyber threats. The working group is divided into 3 levels: Committee level, Management level, and Operation level.
| Governance Level | Role |
|---|---|
| Board Level Audit Committee |
|
| GC Group’ s Digital & IT Steering Committee (DISC) |
|
| ISMS Committee |
|
| Enterprise Architecture (EA Committee) |
|
| Chief Information Security Officer: CISO |
|
| Management Level |
|
| Operation Level |
|
Information Security and Cybersecurity Awareness
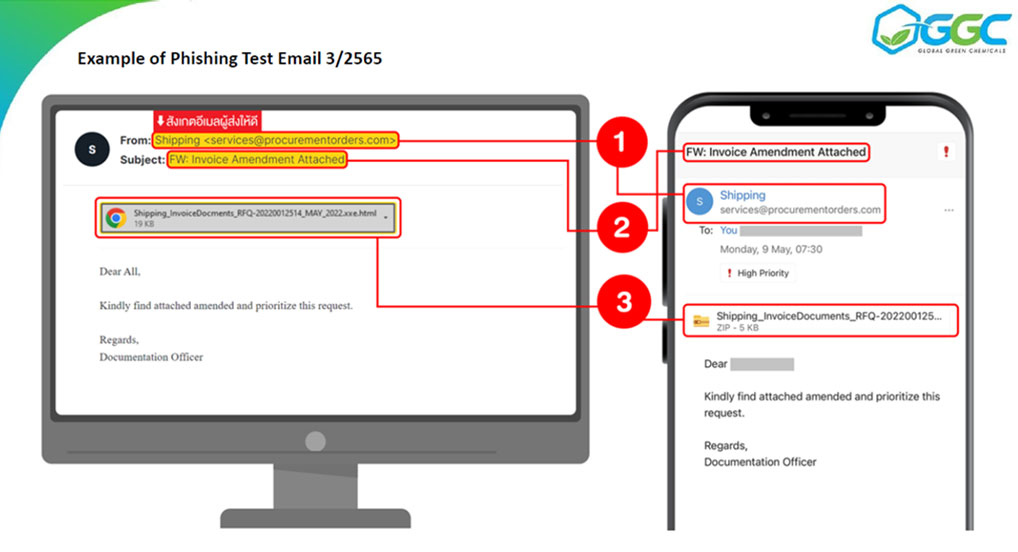
The Company raises awareness and prepares employees regarding cybersecurity at all levels through the knowledge testing, understanding and aware of e-mail based threats (Phishing Test) and 3 E-Learning Cyber Security Online lessons, with an understanding assessment through a post-test at the end of the lesson. Employees can apply the knowledge gained in their work.
1. Cybersecurity Case study: e-mail based threats

2. Maintaining security on personal devices

3. Protection of personal information

Phishing Test in 2023
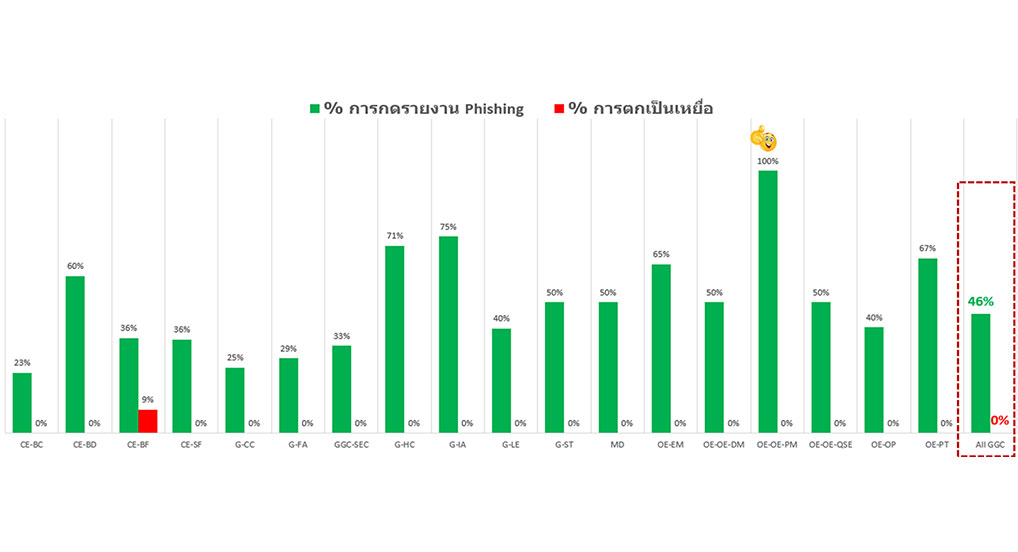
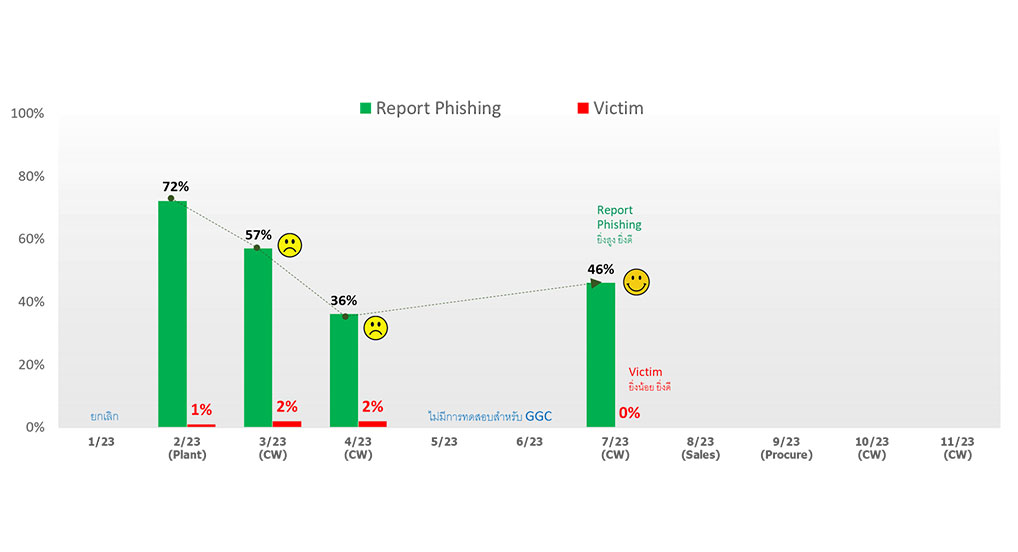
In 2023, it was found that out of a total of 265 employees who participated in the test, 121 employees accurately reported phishing incidents, accounting for 46 percent of all participants. Additionally, one employee fell victim to phishing email, constituting 0 percent of the total. When compared to the previous test, the number of employees accurately reporting phishing incidents increased from 36 to 46 percent, while the number of victims decreased from 2 to 0 percent.

Process and Infrastructure

GGC has established an information security management system and asset security practices according to international standards and in compliance with cybersecurity practices. GGC also conducts annual inspections and reviews of the information and cyber infrastructure systems by external agencies. The past year’s review found that the process and infrastructure of GGC’s information and cyber systems meet international standards and do not have any defects.
In addition, GGC conducts a vulnerability assessment (VA) at least twice a year, the company implements a Business Continuity Plan. In 2023, GGC conducted its annual Cyber Incident Response Tabletop Exercise to test the stability of data security and information technology systems. A simulated scenario of a Cyber Attack was create by an external intrusion, who tries to penetrates GGC’s IT Security in order to gather company’s, leading to company data leakage.
In addition, GGC inspects for internal and external computer system vulnerabilities every 6 months in order to prepare a plan for protection and remediation from threats. GGC’s vulnerability severity levels are categorized into three levels: High Severity, Medium Severity and Low Severity.





